Blog prevention
ISO27002:2022 explained – Physical controls
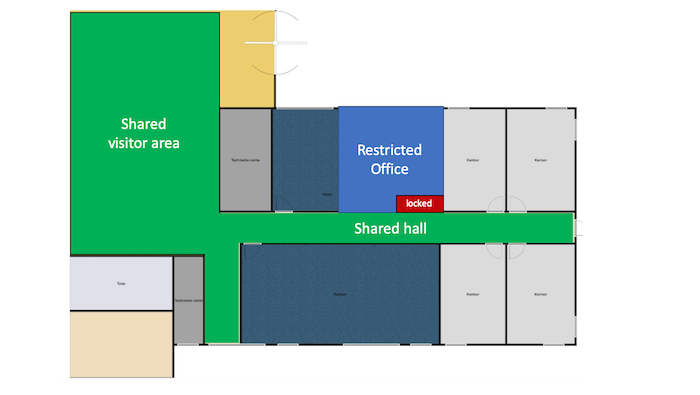
In this article, we explain the new ISO 27002:2022 chapter 7 – Physical controls. This covers the controls necessary to protect information from physical threats. This is the third article in a series of four, each article covering one chapter: organization controls (chapter 5) people controls (chapter 6) physical controls (chapter 7)- This article technological…
Suzanne Atkins
No More Ransom: the best anti-ransomware available
No More Ransom is both the name and the endgoal for a cooperation between the Dutch police and several security companies like McAfee and Kaspersky. The project has been running for more than a year now, and is becoming quite successful in fighting ransomware – but is it enough to fight the currently so devastating flood of…
Tijs Hofmans
How to protect your company from Friday afternoon hacks
Some of the most daring and lucrative cyber attacks are the so-called friday-afternoon scams. As the name suggests, they are often planned just before the weekend when people are most distracted and are based on social manipulation rather than technology.
Sieuwert van Otterloo
Advanced Malware Detection
Malware threats have taken a whole new approach in the past few years. Studying some of them recently in the Digital Crimes Unit (DCU) of Microsoft in Seattle, our thoughts have been confirmed that we have now entered a new era of more sophisticated malware.
Floris van den Broek
