ISO27002:2022 explained – Physical controls
| Suzanne Atkins |
Security
In this article, we explain the new ISO 27002:2022 chapter 7 – Physical controls. This covers the controls necessary to protect information from physical threats. This is the third article in a series of four, each article covering one chapter:
- organization controls (chapter 5)
- people controls (chapter 6)
- physical controls (chapter 7)- This article
- technological controls (chapter 8)
In the previous version, ISO 27002:2013, these controls were mostly in chapters 8 and 11. As we described in this overview article, a few new controls have been added in 2022. A detailed explanation of the previous controls can be found in this blog post.
Physical security perimeter (7.1)
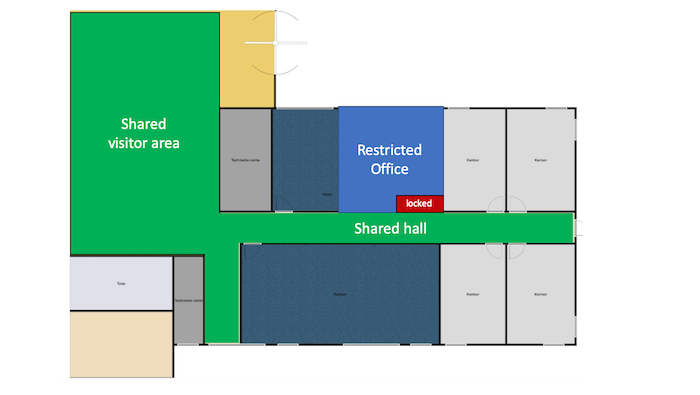
The first step when protecting a physical space is to define its perimeter. Sensitive or critical areas within the perimeter can then be identified. The perimeter must be sufficiently physically secure to protect the contents, with alarms and intruder detection systems. If necessary a monitored reception can control access. The image at the top of this article is an example of a zone plan showing perimeter and secure areas.
Physical entry controls (7.2)
Only authorized persons should be able to gain entry to assets and information. The level of restrictions depends on the organizational requirements. Things to consider include personal identification and logging who accesses the premises. A procedure should be in place for receiving visitors to establish their identity, where they are can go and if they must be accompanied. Deliveries also present a risk, both because delivery areas need to be secured and to prevent delivery personnel entering restricted areas.
Securing offices, rooms and facilities (7.3)
Offices need to be secured with digital or physical keys. In general, detailed directories and maps should not be openly accessible as these can highlight the location of sensitive assets.
Physical security monitoring (7.4)
Monitoring can deter intruders and detect intrusion. Guards, cameras and alarms all monitor against unauthorized access. The design of any monitoring system should be considered confidential. Regular testing is required to ensure that the system works. Camera surveillance systems and other monitoring systems that collect personal information or may be used to track individual may require special consideration under data protection laws. For example, camera surveillance may require a data protection impact assessment under GDPR legislation.
Protecting against physical and environmental threats (7.5)
Natural or manmade disasters and physical attacks threaten information security and business continuity. The level of these risks is highly dependent on location. Floods, fires and large storms are the most likely risks, but the risk from earthquakes, civil unrest and terrorist attacks can also be considered in risk assessments.
Working in secure areas (7.6)
The existence and purpose of secure environments should only be shared on a need-to-know basis. They should be kept locked, with access limited to authorised persons. Generally, lone-working should be discouraged, for both safety and for security purposes.
Clear desk and clear screen (7.7)
Sensitive information left on desks, screens, printers and whiteboards can be accessed by anyone. a clear desk and screen policy defines how and where information can be accessed. A basic policy includes no printed documents left unattended, either at workspaces or printers (clear desk) and locked device screens (clear screen). More detailed policies may be required for sensitive information, for example that information cannot be viewed on a screen in an open environment.
Equipment siting and protection (7.8)
Careful citing of equipment can minimize a host of risks: not just unauthorized access but also the risks due to environmental factors, spilled food and drink, vandalism, and degradation due to light or humidity. The protection required will depend on the sensitivity of the equipment.
Security of assets off-premises (7.9)
Devices, including private devices (bring-your-own-devices), still need protection when they leave the premises. Basics include appropriate physical protection such as covers and theft prevention by not leaving devices unattended. The organization should be aware of what devices are used off premises, by whom, and what information is being accessed or used when off-site.
Storage media (7.10)
Information stored in any media format brings the risk of unauthorized access, and loss of information integrity through modification or degradation, loss, destruction or removal. Media should therefore be safely stored and eventually securely destroyed. Policies governing the management of removable media should cover what information can be stored on removable media, the registration and tracking of such media, how it should be safely stored to prevent unauthorised access or degradation, and how it should be transported. When storage is no longer required, secure destruction is necessary. This may be performed by an external party.
Supporting utilities (7.11)
Power failures can immediately compromise a business’s activities. Less obviously, telecommunications and air conditioning will all interrupt digital activities, and failures of gas, sewage or water supplies will prevent employees from working on-site. Inspection and alarms systems can identify actual or potential failures. Continuity plans should identify back-up options and emergency contact details for service providers.
Cabling security (7.12)
Information and data are transferred via cables, while computers, security systems and environmental controls all require power, supplied by cabling. The former can be intercepted and outages of either can compromise information security and business continuity. The degree of security required depends on the organization, and in many cases will be managed by building facilities providers or telecoms and utilities companies. Basic protections include using cabling conduits or cable floor covers to prevent damage, and locked access to utility access and entry points.
Equipment maintenance (7.13)
Equipment maintenance introduces two information security considerations: poorly maintained equipment risks the loss of information; while equipment servicing or maintenance can expose information to external or unauthorized parties. Regularly serviced and updated equipment is less likely to require riskier repairs or to lead to outages. When repairs are required, care should be taken in choosing service providers and checking their work.
Secure disposal or re-use of equipment (7.14)
Equipment that is no longer in use may still have licensed software installed or stored sensitive data. This also applies to equipment that requires repair, and should be a consideration when deciding whether to use external repair services. Standard delete functions may not be adequate to remove sensitive information. Instead, specialist destruction, deletion or overwriting methods reduce the risk of residual information remaining on the storage media. Remember to remove physical labels or markings too!
Each control measure in ISO 27002:2022 has guidance and implementation suggestions beyond what is summarised in this article. For further information, we therefore recommend reading the norm itself. For a summary of the other chapters in ISO 27002:2022, please visit out blog posts on chapter 5 – organisational controls, chapter 6 – people controls and chapter 8 – technological controls.
Dr. Suzanne Atkins is a geophysics researcher and was consultant at ICT Institute from 2021-2022. She is now working at TNO as machine learning expert in Geophysics.

