Blog Security
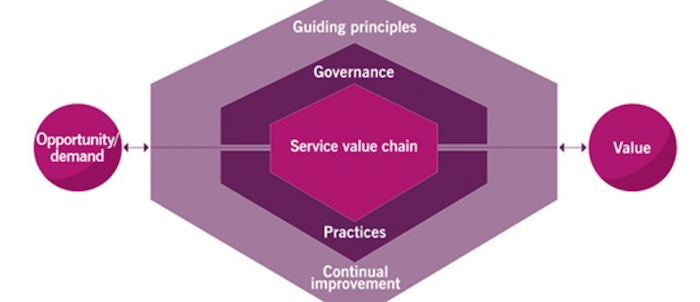
ITIL and service management: a short introduction
ITIL, the standard for service management, is an important standard for people who want to understand how IT is used in practice. It is especially important for professionals that want to grow beyond software development into IT management, since it complements software development really well.
Sieuwert van Otterloo
open standard Security Verified updated
Last month (feb 2024), the 2024 version of the open information security standard ‘Security Verified’ was released. This new version contains small changes to make it more readable and easier to combine with the latest version of ISO 27001.
Sieuwert van Otterloo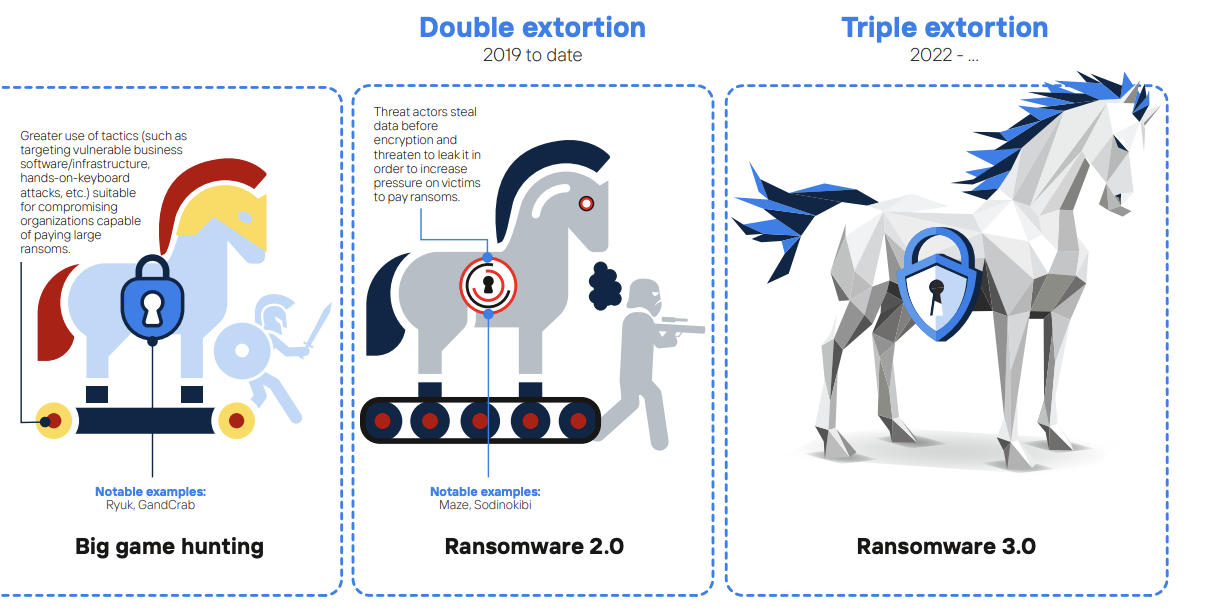
NOREA recommends CIS controls against ransomware
NOREA, the Dutch professional organisation of IT auditors, has conducted a study into a framework for ransomware measures, in response to the increasing ransomware attacks that have been reported in the news, both internationally and in the Netherlands. The use of ransomware has been around for quite some time, however it is very evident that…
Yasmine Yachou
The NIS-2 Directive: raising the security bar in Europe
In the final days of December 2022, a new Information Security Directive has been published by the European Commission. The NIS-2 Directives, aimed at improving the resilience of Europe’s Network and Information Systems, succeeds and supersedes its older brother by both broadening the scope and taking into account the ever changing information security landscape. In…
Joost Krapels
Security+ explanation and practice questions
Security+ is a certification offered by CompTIA. Those who have passed the exam, keep earning Continuous Education points, and pay the annual maintenance fee may add the title to their name. I (Joost) passed this exam recently and wanted to give you an impression of Security+, why you too might want to get certified, an…
Joost Krapels
