Security Verified

Security Verified is an open standard for the information security of organisations, that was created as a light weigth alternative to ISO 27001 and other existing standards. The latest version is Security Verified 2024.
Security Verified: an open standard
Security Verified was created in summer 2016, to fulfil the need of small and midsize technology companies to be certified for Information Security and privacy. Many existing standards, such as ISO 27001, NEN7510, BIO, PCI DSS, ISO 9001 and many privacy certifications are either complex and expensive, do not cover information security completely or are not open standards. ICT Institute has therefore created the open standard Security Verified as an alternative. Anyone can download and use these standards. The standard has been designed to be compatible with ISO 27001 standards so that organisations can start with Security Verified and later transitions to ISO 27001, BIO or NEN7510. Security Verified includes GDPR compliance checks and can be combined with other legal requirements such as NIS2 or AI act. ICT Institute provides auditing and maintains a certification register. You can however also ask other auditors to use the Security Verified standard. The standard is usable by anyone with audit qualifications such as ISO 27001 lead auditor or CISA.
Changes in the Security Verified 2024 version
The Security Verified is updated every 2-3 year to reflect changes in the information security field. In the previous update (2021), several GDPR requirements were included in Security Verified (you can see the previous version here: Security Verified requirements 2021.1). In 2024, Security verified was updated to make it easier to to use both Security Verified and ISO 27001:2022. The order of the requirements has been changed and simplified, the order of the controls is the same and reference numbers have been added. Organisations can still use the 2021 versions if they prefer: the versions have many common elements. For new organisations we recommend the latest 2024 version.
Security Verified structure
Security Verified 2024, like the previous versions, consists of two parts: Part A (chapters 1-4) and part B (chapters 5-8):
- Part A contains 22 requirements that are fully mandatory. Each requirements must be fulfilled. Part A consists of chapters 1,2,3 and 4.
- Part B contains example controls that are all recommended, but you can skip some of these if they do not apply to your organisation. For instance there is a control about software development that you can skip if you do not develop software. It has chapters 5, 6,7 and 8. An organisation must demonstrate the implementation of at least 50% of the recommended controls to qualify for Security Verified certification.
This structure was chosen to make the standard meaningful (real effort is needed and the audit checks many important points) but also flexible enough to work for many different organisations.
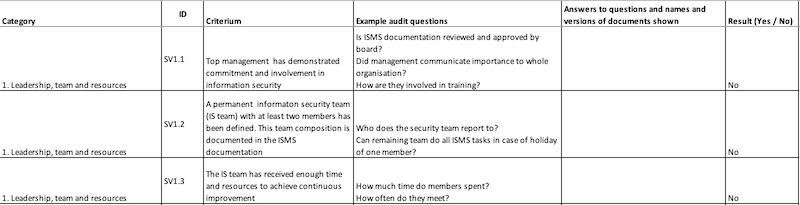
The standard is published in an excel format, that can be used during internal or external audits. You can download the full standard here:
Standard elements
The standard consists of the following elements
- The official checklist: Security Verified requirements EN 2024 and the Dutch version: Security Verified requirements NL 2024
- The Security Verified certificate register– This list allows anyone to check which organisations have obtained a certificate.
- The information security review process used for checking whether organisations qualify for a certificate.
- Information security resources, including standards, innovative companies and professional organisations.
Team, sharing and logos
 The standard is maintained by the ICT Institute information security team and a small advisory board, consisting of several experts including Sieuwert van Otterloo, Jelle Hoekstra, Joost Krapels and Nico Brand.
The standard is maintained by the ICT Institute information security team and a small advisory board, consisting of several experts including Sieuwert van Otterloo, Jelle Hoekstra, Joost Krapels and Nico Brand.
All material of the standard is can be shared under a creative commons license. Specifically anyone can use the requirements checklist as a guideline for audits or reviews of their own information security management system.
The Security Verified logo and name can be used by organisations that have a security verified certificate to refer to their certificate. For more details and the full color logo, see the Security Verified register.