Information security resources

This page is a continuously updated list of information security resources that any information security team member should be aware off. You can contribute to the list by emailing Sieuwert van Otterloo (sieuwert @ ictinstitute.nl).
Information security standards
SANS Institute
SANS Institute and the center for internet security joined forces with the US government to create a list of cybersecurity best practices that are most effective. The list is currently in version 6.1 and contains many useful best practices, ranging from firewalls to secure development.
ISO 27001 and 27002 information security standards
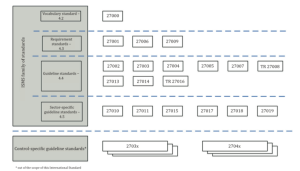 The International Standards Organisations ISO maintains thousands of standards, from very general ‘quality standards’ to very specific technical standards for watches or railways. The ISO 27000 series (wikipedia) is a series of standards that address information security. The first document, ISO 27000, provides basic definitions of security terms. ISO 27001 provides the criteria of a good information security management system, similar to the Security Verified general requirements. ISO 27002 is a list of best practices applicable to most organisations. They are not officially mandatory, but in practice organisations that want to get certified should check all of these controls carefully and consider implementing them. ISO27000 can be downloaded free of charge here. The other standards should be bought from ISO or a national standards body such as BSI or NEN. The image on the right provides a quick overview of the role of all standards in the family (source: ISO27001.
The International Standards Organisations ISO maintains thousands of standards, from very general ‘quality standards’ to very specific technical standards for watches or railways. The ISO 27000 series (wikipedia) is a series of standards that address information security. The first document, ISO 27000, provides basic definitions of security terms. ISO 27001 provides the criteria of a good information security management system, similar to the Security Verified general requirements. ISO 27002 is a list of best practices applicable to most organisations. They are not officially mandatory, but in practice organisations that want to get certified should check all of these controls carefully and consider implementing them. ISO27000 can be downloaded free of charge here. The other standards should be bought from ISO or a national standards body such as BSI or NEN. The image on the right provides a quick overview of the role of all standards in the family (source: ISO27001.
Vulnerability information
The Open Web Application Security Project is an initiative to share information on securing internet-connected systems. The initiative was started in 2001 and is most famous for its publication of the OWASP Top 10, a lits of the ten most vulnerabilities in Internet applications. The OWASP foundation also offers many other resources, such as cheat sheets for developers. The OWASP top 10 is often used as a standard for security tests: any system offered on the Internet should at least be designed to not contain these common vulnerabilities.
CWE/SANS maintains a similar list, called the Top 25 most dangerous software errors.
PCI-DSS
PCI-DSS stands for Payment Card Industry Data Security Standards. It is an initiative by the major banks and credit card providers to increase card data security. Officially the standard is only created for organisations handling credit card data, but the PCI-DSS information is freely available and can be used by other organisations as well. A very useful starting point is the PCI-DSS quick reference guide available here.
Sources of information security news
- The National Vulnerability Database is the largest internet database of known weaknesses in software products. It can be used for checking whether older versions of products are still secure.
- The Amazon security blog is a must read for anyone relying on the Amazon cloud
- The Google security blog provides a lot of information, for instance on issues related to Chrome
- Krebs on security is a blog by information security researcher Brian Krebs.
- The Dutch National Cyber Security Center publishes security advisories for any serious vulnerability.
- If you are using a common webserver or CMS, you should probably subscribe to the security updates for the product. Check here for wordpress, joomla, drupal, apache.
Information security organisations
It is in some case required for information security team members to join the security community. Below is a non-exhaustive list of available organisations.
- The Platform voor Informatie-Beveiliging (PvIB) is a professional organisation for dutch security professionals
- The NGFG is the Dutch professional organisation for Digital Privacy officers
- The IAPP (International Association of Privacy Professionals) is a US-based organisation with local chapters.
ISO 27001 certification auditors
The following organisations can conduct ISO27001 external audits and provide certification
- Digitrust
- Brand Compliance
- Lloyds
If you are considering an ISO27001 audit but are not sure whether you qualify, you can ask ICT Institute to conduct a pre-audit review. We can quickly check whether you have the basic elements in place using our information security review process, and help you become audit-ready.
Interesting but not related initiatives
- Many Dutch IT lawyers specialise in giving good advice on compliance with personal data protection laws and can help with providing the right terms and conditions. Check our overview of IT lawyers in The Netherlands for a list of such lawyers.
Image: Ben White via Unsplash

