Blog

Evaluating the Role of Web Components in 2024: To Use or Not to Use?
In the fast-paced world of web development, it’s essential to keep up with the latest tools and technologies. One such technology is ‘web components’, a way to make reusable components for web apps. Introduced in 2011, they have been supported by all major browsers since 2020. In this blog post, we’ll explore what web components…
Tom Hastjarjanto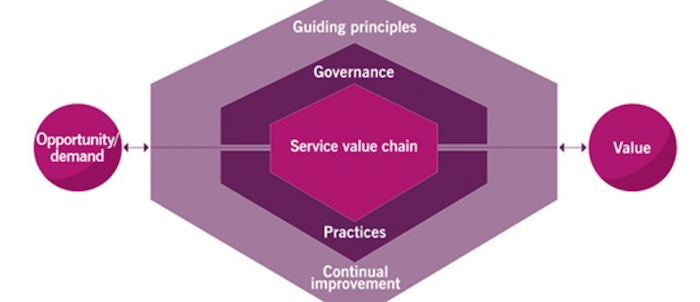
ITIL and service management: a short introduction
ITIL, the standard for service management, is an important standard for people who want to understand how IT is used in practice. It is especially important for professionals that want to grow beyond software development into IT management, since it complements software development really well.
Sieuwert van Otterloo
open standard Security Verified updated
Last month (feb 2024), the 2024 version of the open information security standard ‘Security Verified’ was released. This new version contains small changes to make it more readable and easier to combine with the latest version of ISO 27001.
Sieuwert van Otterloo
Is COBOL futureproof? COBOL in 2024
COBOL is the miracle dinosaur of computer programming languages: It is very old and it should have been replaced by other languages, but somehow it still survives. This causes problems for companies, since many COBOL programmers are retired or will retire in the next decades, leaving companies without anyone to maintain some of the most…
Sieuwert van Otterloo
VU university business track research projects
The Vrije Universiteit Business Track is a novel way for third year Computer Science students to complete their thesis. Instead of working individually on a purely academic problem, in this track they will work in small groups on a real business problem at a real company. We are looking for eight innovative companies with a…
Sieuwert van Otterloo
