Blog malware

What are the Spectre and Meltdown threats?
Security researchers have recently uncovered security issues known as Meltdown and Spectre. These issues apply to all modern processors and allow attackers to gain read access to parts of memory that were meant to be secret. To initiate a Spectre- or Meltdown-based attack, the attacker must be able to run code on the victim’s processor. What are Spectre and…
Floris van den Broek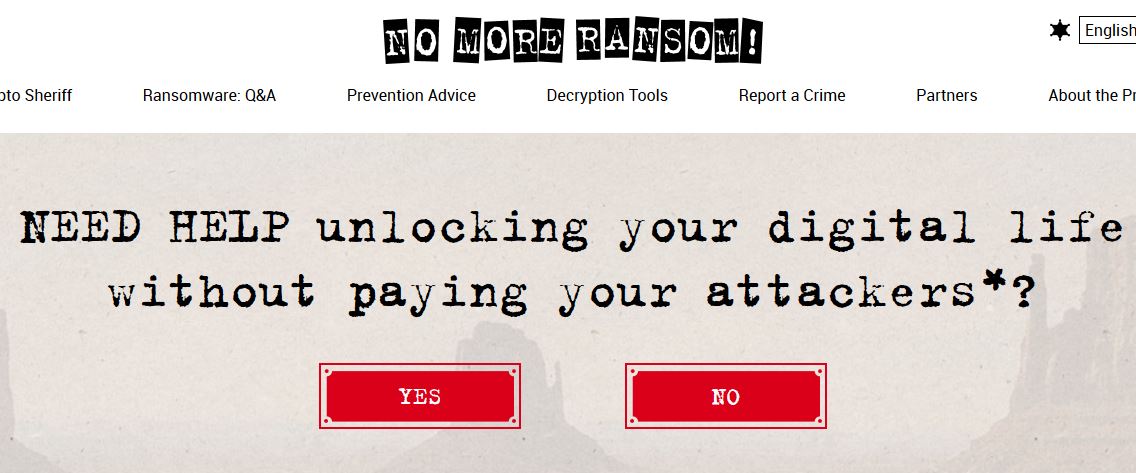
No More Ransom: the best anti-ransomware available
No More Ransom is both the name and the endgoal for a cooperation between the Dutch police and several security companies like McAfee and Kaspersky. The project has been running for more than a year now, and is becoming quite successful in fighting ransomware – but is it enough to fight the currently so devastating flood of…
Tijs Hofmans
Cyber security trend analysis – network scanning data
The number of malware-treats, viruses and other cyberattacks reported in the media is on the rise, due to two factors: the media have become more aware of the important real world impact of cyber criminals, and international police officers are getting better at capturing large criminal networks. But does this mean that cyber crime is…
Sieuwert van Otterloo
Advanced Malware Detection
Malware threats have taken a whole new approach in the past few years. Studying some of them recently in the Digital Crimes Unit (DCU) of Microsoft in Seattle, our thoughts have been confirmed that we have now entered a new era of more sophisticated malware.
Floris van den Broek
