Cyber security trend analysis – network scanning data
| Sieuwert van Otterloo |
Security

The number of malware-treats, viruses and other cyberattacks reported in the media is on the rise, due to two factors: the media have become more aware of the important real world impact of cyber criminals, and international police officers are getting better at capturing large criminal networks. But does this mean that cyber crime is under control, or is the number of attacks also rising? We analysed a quarterly trend report from RedSocks, one of the most innovative IT security firms, to answer this question.
Putting media attention in perspective
The current cyber security industry suffers from a ‘rockstar’ syndrome: while the industry does get the media attention that is needed to increase public awareness, the attention is not distributed evenly: a few ‘rockstars’ (major events and international incidents) get all the attention, while much more common but less high-profile threats are ignored. This media bias makes it hard for top management to get a complete perspective and understand the practical threats that are relevant to their company. To get the full picture, one must dig deeper. Luckily, several cyber security research publish annual and quarterly reports with insights in threats. One of these companies is RedSocks. This Dutch company makes devices that monitor network traffic for companies, scanning for all kinds of malicious activities. Any suspicious file is isolated, stored and analysed by RedSocks so that if it is malware or a virus, it can be blocked in the future. In their quarterly report they list the overall number of files stored and analysed, giving a unique perspective in cybercrime trends.
Types of threats
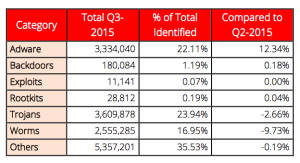 One of the most interesting tables in the report is an analysis of types of threats. There are now many different types of malware, each with their own categories. RedSocks uses seven main categories:
One of the most interesting tables in the report is an analysis of types of threats. There are now many different types of malware, each with their own categories. RedSocks uses seven main categories:
- Adware: installs itself in browsers and shows additional adds to users (without paying the website owner whose content is blocked by ads)
- Backdoors: This software makes it possible for hackers to enter the infected computer and steal data
- Exploits: attack scripts aimed at a specific security weaknesses. If they reach the target, they can often take over the computer.
- Rootkits: Rootkits help to hide malware on computer. Once a rootkit is installed, the malware is no longer visible
- Trojans: A Trojan horse (named after the Ancient story) is installed by the user itself but does something else than the user expects.
- Worms: Worms are computer scripts that can copy themselves, spreading through a network without permission from users.
- Other: anything else that is harmful. Often a combination of the above.
The biggest rise compared to the third quarter of last year is in the adware category. This category could be considered more of nuisance than a real threat for users, but it can be a real moneymaker for organisations. Hopefully makers of insecure browsers improve their software and make adware impossible.
Overall trend
The overall trend for malware is flat: while the amount of internet traffic has increased, the amount of malware stopped by RedSocks is about the same. The graphic below shows the number of unique malicious files found. About 3000-5000 new files are found each month.
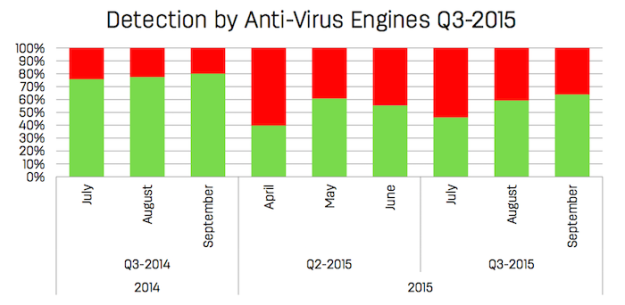
Network scanning versus anti-virus
One of the most interesting analysis is the comparison of traditional virus scanners versus network scanning. Certain threats are hard to detect for virus scanners since they hide as user content, but can more easily be identified by network scanners based on the traffic they generate. The chart below shows the detection rates of various virus scanners against all the malware found. As you can see, the virus scanners are not 100% successful. The trend changes month to month: undetected threats can grow large quickly, but disappear immediately when the major virus scanners are updated.
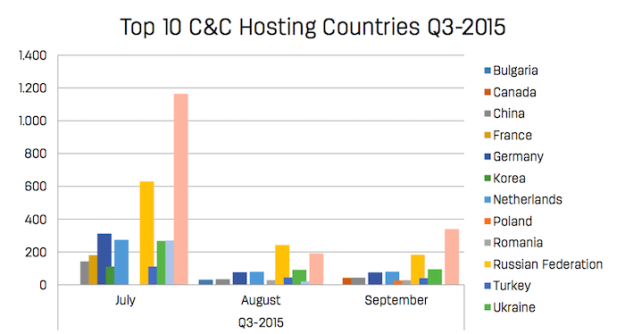
The Netherlands
As a result of their scanning activities, RedSocks can also see which countries host most malware. Russia is the overall winner (yellow), but The Netherlands is also listed in this top-12.
Recommendations
The full report can be found at the RedSocks website. We recommend any company to have a firewall and virus scanning in place: these are basic steps that are even mandatory in many sectors. For companies that already have these in place, we recommend to check the log files regularly and see if and what kind of threats are detected, and also conduct an analysis of traffic per country. If you do see an unusual pattern, it might be wise to change the settings or even add additional scanning tools.
Dr. Sieuwert van Otterloo is a court-certified IT expert with interests in agile, security, software research and IT-contracts.