Blog verified

open standard Security Verified updated
Last month (feb 2024), the 2024 version of the open information security standard ‘Security Verified’ was released. This new version contains small changes to make it more readable and easier to combine with the latest version of ISO 27001.
Sieuwert van Otterloo
New 2018 version of Security Verified standard
The open standard ‘Security Verified’, has been updated in August 2018. It is a minor update to improve readability and to make the standard fully aligned with GDPR. The recent update should make this standard even easier to use for organisations that want a good Information Security Policy based on the same principle as ISO…
Sieuwert van Otterloo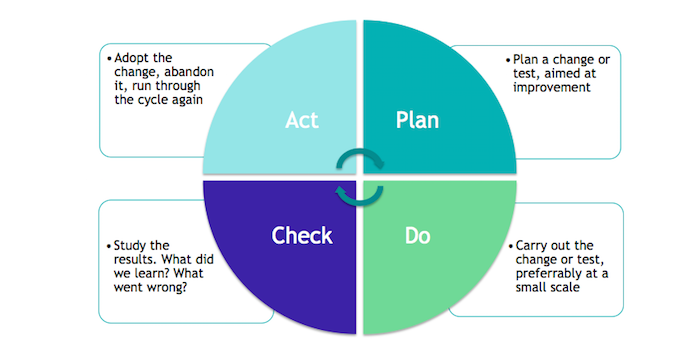
Information security and PDCA (Plan-Do-Check-Act)
Standards such as ISO 27001 require you to use a method for continuous improvement in your information security policy. PDCA or Plan-Do-Check-Act is the preferred method for most information security teams and we recommend you to use this method, described in this article.
Sieuwert van Otterloo
Information security – Cryptographic controls policy example
Using cryptographic controls such as encryption can help with information security, but only if it is applied correctly. To make sure it is used in the right way, it is recommended by standards such as ISO 27002 have a data encryption policy. In this article we share the ICT Institute data encryption policy, that is…
Sieuwert van Otterloo
