NOREA recommends CIS controls against ransomware
| Yasmine Yachou |
Security
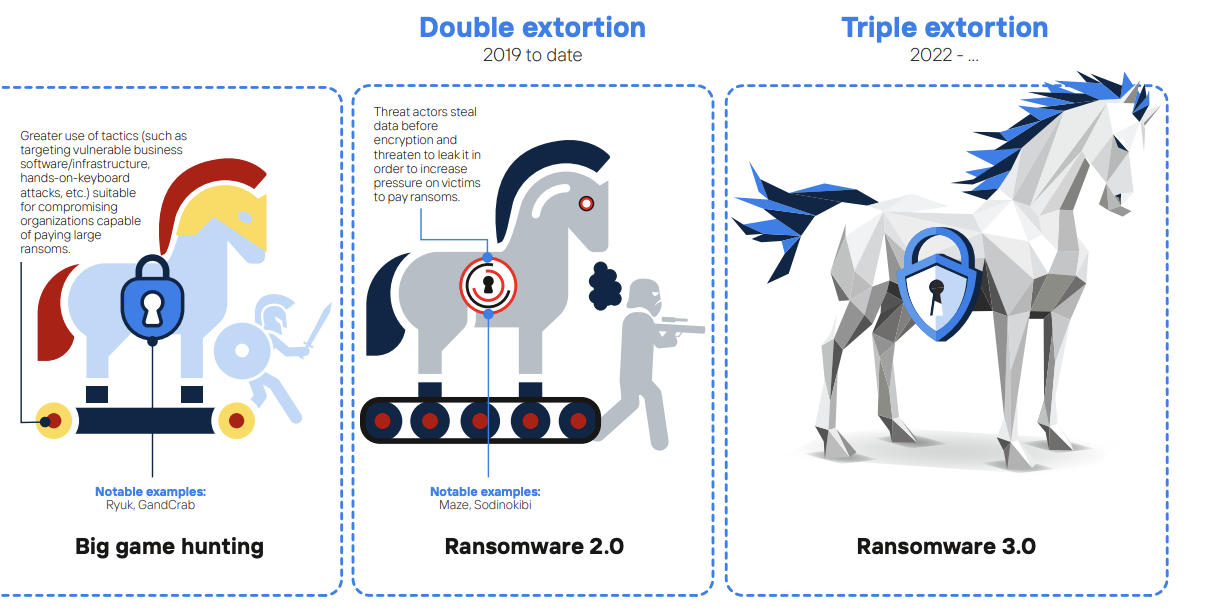
 NOREA, the Dutch professional organisation of IT auditors, has conducted a study into a framework for ransomware measures, in response to the increasing ransomware attacks that have been reported in the news, both internationally and in the Netherlands. The use of ransomware has been around for quite some time, however it is very evident that there has been a significant increase of ransomware attacks since the COVID-19 period ,as a result of hybrid working. It is also constantly evolving, with 2020 bringing forth the evolution of ransomware 2.0 (double-extortion), whereas currently, as of 2023, it is already evolving into the early stages of ransomware 3.0 (triple-extortion). The study conducted by NOREA, as well as the associated framework with measures, are publicly available: Ransomware in control a study report by NOREA.
NOREA, the Dutch professional organisation of IT auditors, has conducted a study into a framework for ransomware measures, in response to the increasing ransomware attacks that have been reported in the news, both internationally and in the Netherlands. The use of ransomware has been around for quite some time, however it is very evident that there has been a significant increase of ransomware attacks since the COVID-19 period ,as a result of hybrid working. It is also constantly evolving, with 2020 bringing forth the evolution of ransomware 2.0 (double-extortion), whereas currently, as of 2023, it is already evolving into the early stages of ransomware 3.0 (triple-extortion). The study conducted by NOREA, as well as the associated framework with measures, are publicly available: Ransomware in control a study report by NOREA.
The framework developed by NOREA aims to help organisations in their defence against ransomware, using the Critical Security Controls Version 8, by selecting the most relevant controls in order to achieve a safer digital world. The CIS controls are known as high-priority and effective defensive actions that can be taking by organisations in order to improve their cyber defense. The controls were initially developed by Sans Institute, recognised for its training and certification programs, and were formally known as the Sans Critical Controls. The current version 8, has been updated in 2021 and currently consists of 153 different defensive actions.
Kill chains: how to analyse an attack
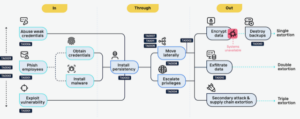
The report describes several kill chains. In order to carry out a successful attack, the kill chain is used to analyse an adversary’s end-to-end attack proces and break those actions down into discrete conceptual phases. This allows organisations to apply targeted controls to defend itself for each phase by analysing the links between the phases, allowing it to identify points in the attack pattern and break the chain that leads to the attack. The organisations may be able to stop the attack completely or at least significantly reduce the damhage if one of these processes is interrupted. The following kill chains have been described:
- NCSC kill chain consists of five steps: getting acces to the target’s network, strengthening the position in the network through installing malware, steal information to try to maximise ransom, blocking access and encrypting files and lastly negotiating the ransom and obtaining the decryption key.
- Unified Kill Chain, which lists 18 tactical steps that can be followed for an attack to be successful. However, not every step has to be used in every attack. The Unified Kill Chain outlines three phases (In, Through, and Out) to accomplish the
- goal, as well as many attack tactics.
- Northwave kill chain, which also makes use of the 18 tactical steps described in the Unified Kill Chain, as well as the three phases, where the first phase signifies trying to gain access to the network, the second phase signifies having successfully penetrated, while trying to remain ‘unseen’, and the last phase, which signifies data exfiltration and data encryption.
From analysing these three ransomware kill chain models, NOREA shows that accessing an organization’s IT infrastructure is the first step in a ransomware assault. An attacker may choose to use multiple attack routes to do this. The following figure gives an overview of the NOREA kill chain, which is based upon the Northwave kill chain, as can been seen from the three phases, with encrypting data and exfiltration of data in the last phase.
The framework: what does it look like
In case an organisation’s cybersecurity maturity level is sufficient, implementing a cybersecurity framework can boost cyber resilience. How well controls can be implemented depends on the maturity level. To reduce the danger and effects of a ransomware attack, organisations should at the very least implement basic security measures. In the report, several frameworks are examined that helps assist organisations in implementing and maintaining existing cybersecurity controls. From this examination, NOREA has concluded that compared to the ISO 27001 and NIST-CSF frameworks, the CIS architecture is more focused on implementing technical and operational cybersecurity controls, and therefore concludes that it can make the strongest contribution when it comes to developing a ransomware framework that IT professionals can use right away.
NOREA presents their own ransomware kill chain in this report, as existing kill chains seem to not adequately represent the most recent advances when it comes to how ransomware attacks are executed. They have created a model based on the Northwave kill chain, as it is very simple and represents the most common attack vectors that are used. As stated previously, the framework is based mostly on the CIS V8 controls. However, several additions have also been made to the framework, in attempt to best help protect against ransomware. The following additions are mentioned in the report:
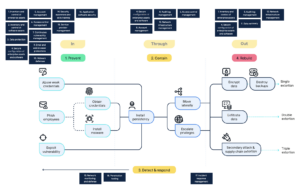
- A selection has been made of CIS controls that are deemed most relevant when it comes to protecting against ransomware. Out of the 153 CIS V8 controls, 89 controls have been selected for the framework, such as requiring MFA for remote network access, deleting or disabling any dormant accounts after a period of 45 days of inactivity, and lastly centralizing access control for all enterprise assets through a directory service or SSO provider.
- The selected controls have been mapped to 12 specific attack steps of the kill chain. Some examples of such steps are: encrypting data, exploiting vulnerabilities and abusing weak credentials.
- In some cases, selected controls are also supplemented with additional specific ransomware control activities. This has been done as the CIS domains fall short when it comes to situations where the IT-environment needs to be rebuilt. Some examples of such activities are: ensuring that the network devices (such as firewalls, VPN, Load balancers) are kept strictly updated and ensuring that firewall rules are documented and regularly reviewed.
- The selected controls are matched to three different main phases of a ransomware attack (in, trough and out)
- The selected controles are mapped to four mitigation strategies (prevent, contain, detect & respons and rebuild)
The figure, taken from the framework report, demonstrates the mapping of the necessary CIS control domains that must be handled for each of the three kill chain phases. The blue blocks above signifies the CIS control domains for each kill phase.
 What is the added value?
What is the added value?
Frameworks like the one constructed in the report, can help organisations build a larger digital resilience by providing relevant controls that help protect these organisations. Although the use of frameworks like these can go a long way, it is still crucial for organisation to increase the digital resilience and stimulate organisation to think about protecting themselves, and therefore think of, not only the potential destruction that ransomware attacks might cause, but also the enormous effort necessary to thwart it.
The framework is mostly built upon the already existing CIS V8 framework, with few additional changes made. This CIS V8 controls are knowns as being widely applicable in the field of IT management. However, for this study, the focus was only on the most relevant controls for managing ransomware attacks. As the Korea framework is freely disseminated, one of its goals is also the continuous improvement of the framework. It is therefore published as an open source tool.
For more articles about information security, visit this page.
Yasmine Yachou has completed both her BSc. and MSc. Information Sciences at the VU Amsterdam. Within ICT Institute, Yasmine works as a consultant, focused on privacy management.