Blog
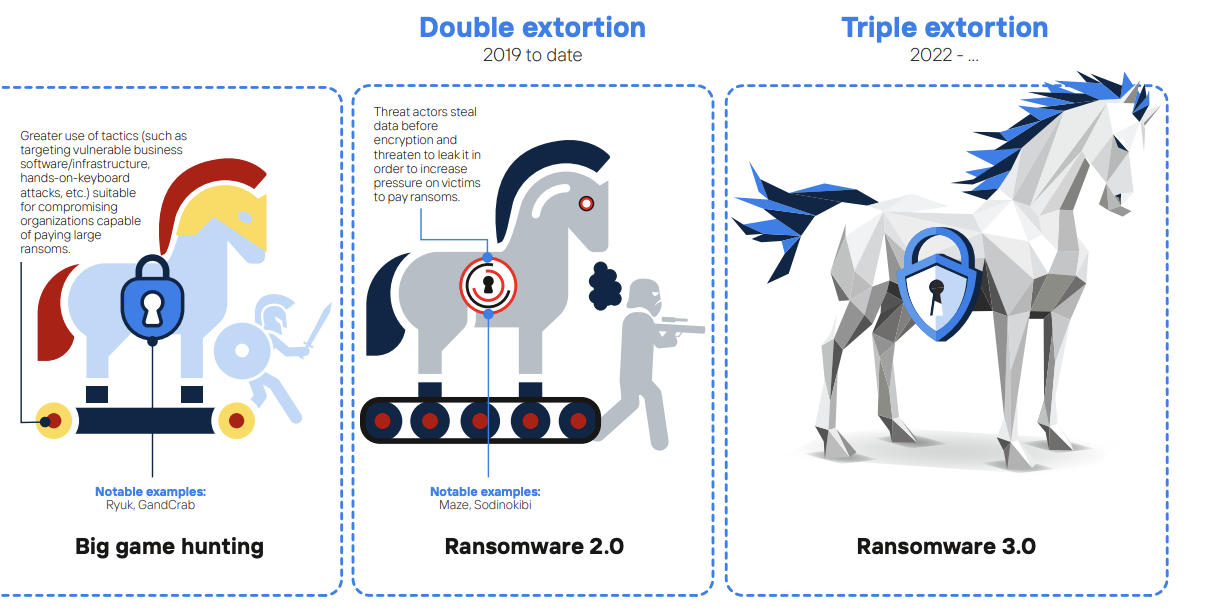
NOREA recommends CIS controls against ransomware
NOREA, the Dutch professional organisation of IT auditors, has conducted a study into a framework for ransomware measures, in response to the increasing ransomware attacks that have been reported in the news, both internationally and in the Netherlands. The use of ransomware has been around for quite some time, however it is very evident that…
Yasmine Yachou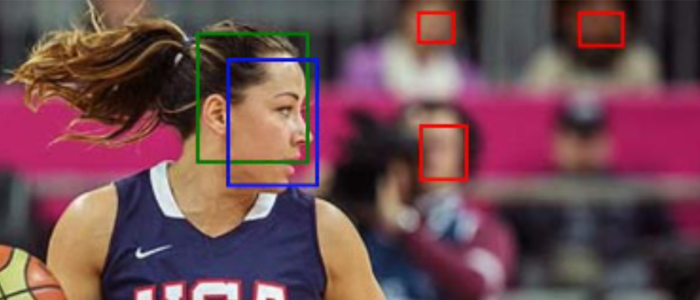
Comparing cloud AI services against open source libraries for face detection
The three large cloud companies Google, Microsoft and Amazon offer cloud services for many AI tasks. Using these services has practical benefits but also strategic risks: when using a service, you have less control over your AI use. In order to gain insight into the pros and cons of AI services, Elif Kalkan has done…
Sieuwert van Otterloo
Legocolor: a computer vision dataset for learning datascience
The Legocolor dataset is a new dataset designed to test common data science techniques such as k-nearest neighbour and decision trees. The dataset consists of color samples (red, green and blue value) from real world images of Lego and the official lego color of the brick, and the goal is to train a model to…
Sieuwert van Otterloo
Staying up to date with python – research survey
Python is one of the most used programming languages: thousands of developers use the language and its frameworks of libraries for new IT systems. The language itself and the various libraries and frameworks are frequently updated and this causes legacy issues: Systems must be changed to work with the latest frameworks,or become vulnerable to security…
Sieuwert van Otterloo
The ICTI list of influential computer scientists
Computer, science, AI and privacy-law are often described as new fields of research. This maybe was the case in 1990, but as of now these fields are old: The solutions to most current problems in society are already invented years ago, but not well-remembered. To help ourselves and other people remember all the work, we…
Sieuwert van Otterloo
