Fewer security vulnerabilities found in 2015
| Sieuwert van Otterloo |
Security
Finally some good news on IT security: The total number of IT security vulnerabilities was 20% lower than in 2014, according to ICT Institute analysis based on CVE data. Apple was the most vulnerable vendor and the iPhone OS and Mac OS X were the most vulnerable products.
This article is based on research by Martin Janek and Sieuwert van Otterloo
Publishing IT vulnerabilities
The IT security world is an on-going battle between ethical hackers and unethical hackers: the ethical hackers are searching for vulnerabilities in IT systems in order to fix them, the unethical hackers use them to mount cyber attacks and create malware. There is an interesting debate whether ethical hackers should publish their findings: on the one hand other people need to know about new vulnerabilities so they can fix them. On the other hand unethical hackers can exploit published vulnerabilities. Most experts believe the benefits of transparency are more important than the disadvantages, and most vulnerabilities are published and added to the CVE: the Common Vulnerabilities and Exposures database. This publicly accessible database contains all known vulnerabilities of popular IT products, and it plays an important role in avoiding redundant work and double reporting in the security industry.
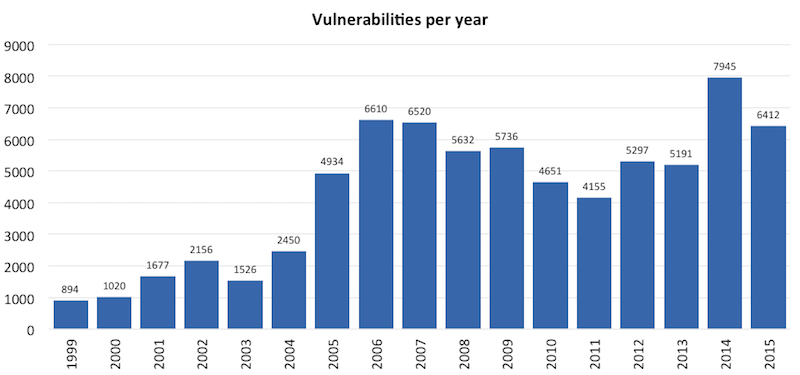
Vulnerabilities per year
The database offers data going back to 2000, when 1020 vulnerabilities were reported. Since then, the number of vulnerabilities have risen steeply. This is due to the fact that more IT systems are used in daily lives, due to increased complexity and connectivity of IT products and due to increased security awareness. In 2014, the worst year so far, almost 8000 vulnerabilities were discovered. The total number for 2015 is 19% lower, with 6412 vulnerabilities. This is still a large number but it is good to see that the data is no longer exploding. Vendors are learning the basics about security.
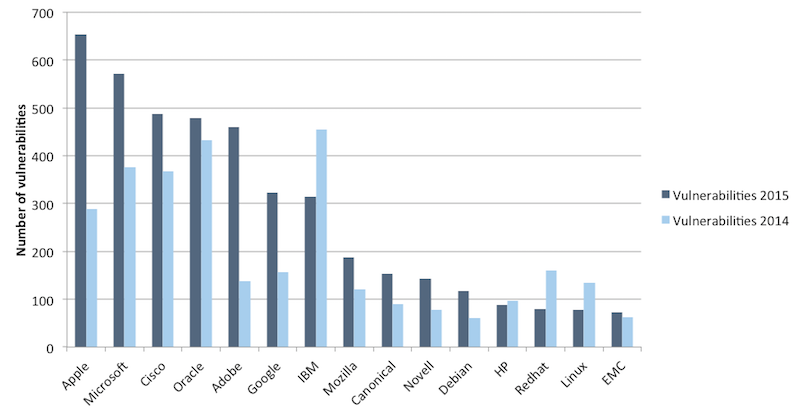
Vulnerabilities per vendor
It is also interesting to compare the number of vulnerabilities per vendor. This says something (but not everything) about the quality process of each vendor. We must stress that the results are not purely about quality: some vendors simply have more products than others. Having said that, here is the top 15, with a comparison to the numbers for the same vendors in 2014.
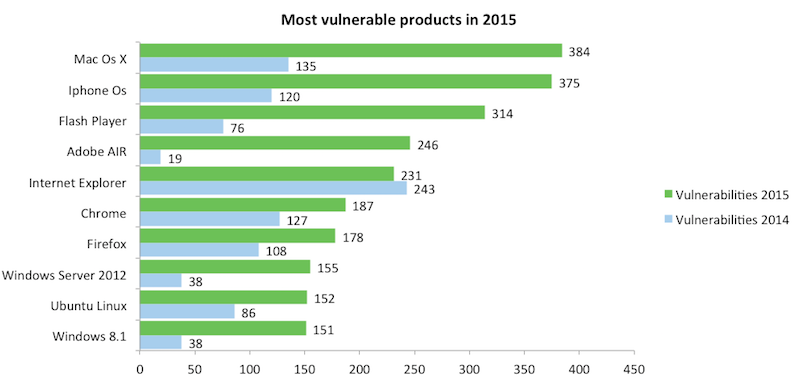
Vulnerabilities per product
This next chart shows the individual products for which most vulnerabilities were found in 2015. In our view, the results are disturbing: individual products should not have more than 20 vulnerabilities per year. The high number of vulnerabilities can be partially explained by the high complexity of each project. Operating systems such as iOS have become so complex that it is hard to fully test the product for all vulnerabilities.
One of the worst products from a security perspective is Abobe Flash. According to experts (including the late Steve Jobs), Flash is simply a very bad product and people should stop using it. See this wired article, or this article on an October security incident. Adobe AIR (a runtime environment for various platforms) seems to do not much better than Flash. It also has way more security vulnerabilities than a modern product should.
Many people are also interested in whether open source products are better or worse than proprietary products from a security perspective. The answer is that it depends on the individual product. There are some open source products in the top 15 (Ubuntu, Chrome, Firefox) but not more than one would expect given the popularity of open source products.
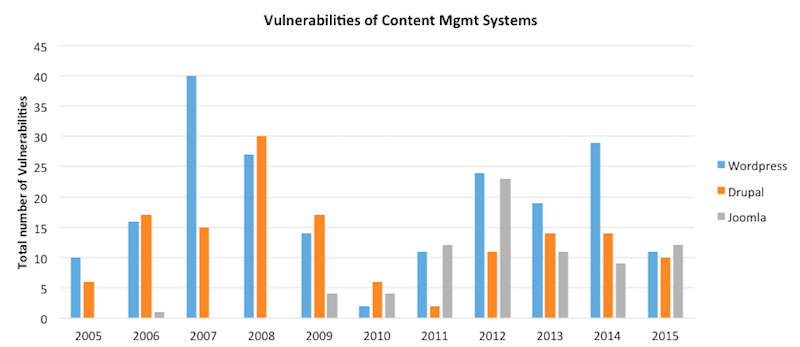
Comparing products
We recommend anyone to check the number and trend of security vulnerabilities before making any product decision. This analysis will not only show the relative security of different products, but will also show which versions are safe and not safe for use. As an example, we made a comparison for the three most popular content management systems (CMS): WordPress, Drupal and Joomla. The results are very evenly matched: each of these systems had around 11 vulnerabilities in 2015.
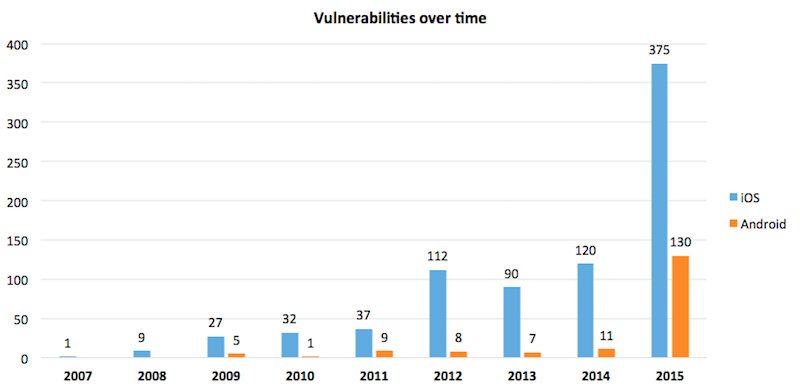
We also compared Android and iOS, the two most popular operating systems for smartphones. The analysis shows a worrying trend, with the number of vulnerabilities in smartphone increasing dramatically: both systems are over our recommended threshold of 20 vulnerabilities per year, and are thus not safe for use. Even though Apple has many more vulnerabilities than Android, the risks are actually highest for Android users. The reason is that many Android manufacturers do not have a good way of pushing security updates to Android users. This means that many vulnerabilities cannot be fixed. Let’s hope Android manufacturers take immediate action to protect their users.
Next steps
Analysing CVE data before using a new product is a highly recommended security measure for any organisation. This should be done in the design phase for each project, and be repeated regularly for all live systems. The CVE database can be found here. A good tool for gathering CVE statistics is CVEdetails.com. We used this tool for our analysis. Of course the analysts of ICT Institute can help with further analysis and advice for most software products. Contact us via the form below for any questions.
Dr. Sieuwert van Otterloo is a court-certified IT expert with interests in agile, security, software research and IT-contracts.