Access Management: an introduction
| Joost Krapels |
Security

Identity and Access Management, or IAM for short, is one of the cornerstones of Information Security. Organisations cannot protect the confidentiality, itegrity and availability of information entrusted to them if it can be seen, altered and deleted by anyone who simply desires to do so. In Information Security, we call the sequential steps required for this Identification, Authentication and Authorization. When a user passes all these succesfully, he or she is granted access. In this article, we introduce you to information access by explaining the core concepts and how they interact. This article is not a technical deep dive, but should give managers tasked with setting up access control, developers new to Information Security, or those planning to attain CISSP certification a good starting basis.
The domain of IAM consists of, as the name suggests, two subdomains: Identity Management and Access Management. In this article we will focus on Access Management, which encompasses all technical and organisational measures you can take to get the right information to the right people safely. Identity Management, on the other hand, focusses on providing the right people with the right access permissions. Since Identity Management requires a deeper understanding of Access Management, it is a topic for another day.
Identity & Access Management is also one of the eight domains you need to master to pass the Certified Information Security Systems Professional (CISSP) exam. For this exam, we provide a free study template. If you are studying for the CISSP exam, just like I am at the moment, you can use this article as a high-level summary and quick refresher on the topic. The Study Guide, which I used a source, does however go a lot deeper and also touches upon authentication in greater detail. Good luck studying!
Provisioning access
Access provisioning is the process of allowing a subject to interact with a certain object. Subjects are always the active partner is this relation, and can be humans, processes, and applications. Objects are entities that contain information, and are interacted with by subjects. Examples of objects are systems, databases, and processes. As you can see, some entities can be the subject in one situation, but the object in another. In some interaction, entities can switch roles. This is, for example, the case when loading a web page in your browser.
- You (subject) ask your browser (object) to show you the website www.ictinstitute.nl;
- The browser (now subject) then queries the server (object) for the web page;
- The server (object) sends the information back to the browser (subject);
- Once the browser receives the new information, it returns to its role as the object and provides you, the subject, the web page you requested.
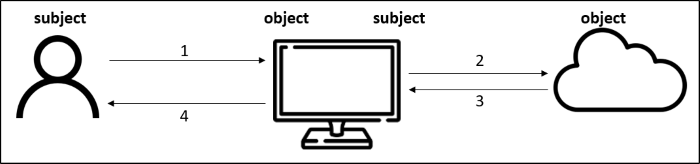
Most information on websites can be accessed as easily as depicted in the figure above. If we forget about networking and the DNS infrastructure for a moment (perhaps a story for another day), accessing information on a website is as easy as telling your browser you want the information, and the browser then retrieves it for you. As we said in the introduction, information is, however, often not meant for just about anybody. Most information systems contain a more strict form of access control, so that only specific individuals or software can access information. The steps required for a subject to gain access to a specific resource at a certain organisation goes as follows:
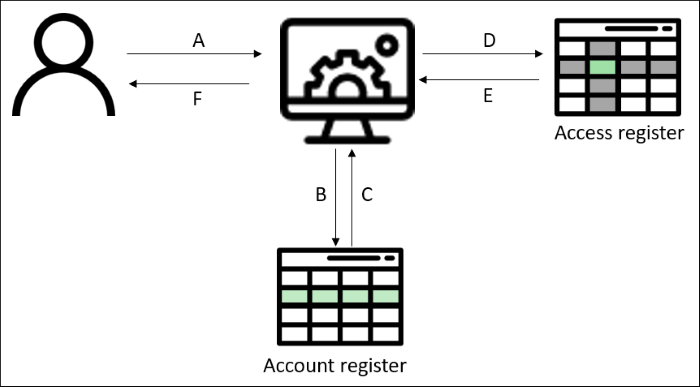
- Identification – Subjects first claim an identity. For me to gain access to my emails, I tell our email provider that I am Joost, and he should know me by the identity joost[at]domain.com. If the system recognizes this identity, the next step follows.
- Authentication – Anybody can claim any identity, so just relying on identity is not enough to secure access to information. Subjects need to prove that they are who they say they are, which is what we call authentication. These days, there are many ways to authenticate yourself. The most common authentication mechanism is a password. The user provides a username and password, which the system checks against its internal database / account register. In case of a match, the user is granted system access.
- Authorization – Even inside information systems, not all users should be able to access all information. This is where the third step comes in. Once a subject requests access to an object, many information systems check an internal access register. The access register states which user (or group of users) may access which resources. If a subject is authorized to access an object, the access is granted by the system. There are countless authorization mechanisms and models, but we will not go in to them further in this article.
Single Sign-On
Organisations often use multiple software systems and software services at the same time. Creating a user account for all services is certainly possible, but is guarranteed to give both the IT-department and employees doing their day to day work a headache. For this reason, Single Sign-On (SSO) is applied more and more. SSO allows users to use the same credentials (e.g. their “work email and password”) for all systems and software. By centralizing the authentication process and having the connected systems trust this authentication, different services can be used with the same credentials. For example, organisations that use Microsofts IAM, Azure Active Directory, can use Azure SSO as the base station to connect other SaaS and even on-premise systems. Some organisations, such as Google and Facebook, even offer SSO to consumers. You might have seen the “Log in with Google” or “Continue with Facebook” on services such as Spotify or your favorite newspaper.
Controlling access
Due to the value of information, access control has become a necessity. Even in the international Security Standard ISO 27001:2013, a whole chapter (A9) has been dedicated to it. Both digitally and physically, malicious actors will try to circumvent the access process to receive access to information not meant for them. There are three main chronological steps the defensive side takes to prevent unauthorized access:
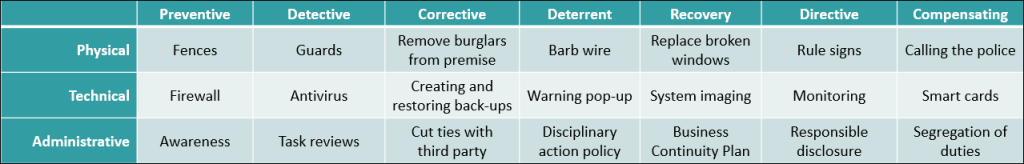
Preventive
The first step in defending against attacks is to prevent the attack from even taking place. Stopping an attacker at the physical or electronic gate can prevent significant damage to your organisation. In the material world, preventive measure can be fences and strong locks on doors but organisational measure such as employee awareness training and separation of duties are very effective as well. Digital preventive controls are firewalls, antivirus software and data encryption.
Detective
You can never fully prevent any and all attacks from happening. If you cannot prevent an attack, the next step to take is to detect it. Detective controls help you to notice an attack is taking place or has taken place. Digital examples are malware scanners, smart monitoring tools such as Microsoft Defender for Identity, and SIEM-systems. Examples in the physical world are guards patrolling, motion sensors, and audits.
Corrective
Once an attack or other type of unauthorized access has taken place, the compromised situation needs to be reverted to the secure standard situation. Corrective controls repair the “damage” that has been done to systems, so that the organisation can continue as safe as or even safer than before. Physical examples include handing over a burgler to the police and replacing locks. In the technical domain, rebooting a system, restoring a back-up, and resetting authentication details are ways to return to the original safe state.
Another common way to categorize access control is Deterrent, Recovery, Directive, and Compensating. Deterrent controls are meant to discourage malicious actions before they take place. Recovery controls are similar to Corrective controls, but are meant for situations where the impact is more severe. Directive controls aim to (positively) force compliance to rules, and sometimes even reward desired behaviour. Finally, Compensating controls are put in place to fill in the gap when original controls cannot or are not executed well. Since they effectively replace an original control, compensating controls may not be weaker than their predecessor.
Implementation methods
As you may have noticed, all examples in the seven categories above fall in either one of three domains. The Physical domain, a.k.a. the real world, the Technical/logical domain, which includes all software and hardware controls, and finally the Administrative domain, which entails all rules and policies organisations put in place. By separating the controls in how they are implemented in practice, it is a lot easier to choose a suitable responsible person/department for the implementation and monitoring of the acces control measures your organisation has in place. In the table below we have provided examples for all possible combinations of control categories found in this article.
Discussion
In the open special interest LinkedIn group Information Security NL we like to discuss the latest news on privacy and security. This article has been posted there as well, and we are curious about your take on the situation. Information Security NL is a free initiative for sharing knowledge on information security. For more articles about information security, visit this page.
Source: Chapple, M. Stewart, J.M. Gibson D. (2018). Certified Information Systems Security Professional Official Study Guide.
Image credit: @CDC via Unsplash
Icons: Flaticon
Joost Krapels has completed his BSc. Artificial Intelligence and MSc. Information Sciences at the VU Amsterdam. Within ICT Institute, Joost provides IT advice to clients, advises clients on Security and Privacy, and further develops our internal tools and templates.