Blog ISO 27001

open standard Security Verified updated
Last month (feb 2024), the 2024 version of the open information security standard ‘Security Verified’ was released. This new version contains small changes to make it more readable and easier to combine with the latest version of ISO 27001.
Sieuwert van Otterloo
Register of suppliers – free template
Suppliers come in all shapes and sizes: utilities, cloud platforms, office facilities, email providers, equipment maintenance, accountants, freelancers, PEN-testers and last but not least, information security consultants like ICT Institute. Your relationship with them should include information security considerations. The security requirements for suppliers depends on the service or product they provide. Your outsourced HR…
Sieuwert van Otterloo
Measuring and monitoring your ISO 27001 ISMS
Measuring and monitoring information security is required under clause 9.1 of ISO 27001. In this article we explain how to effectively monitor and measure your ISMS.
Joost Krapels
ISO27002:2022 explained – Technological controls
In this article, we explain the new ISO 27002:2022 chapter 8 – Technological controls. This covers the controls required to set up and maintain secure technological systems, particularly focusing on secure systems, development and code management. This is the last article in a series of four, each article covering one chapter: organization controls (chapter 5)…
Suzanne Atkins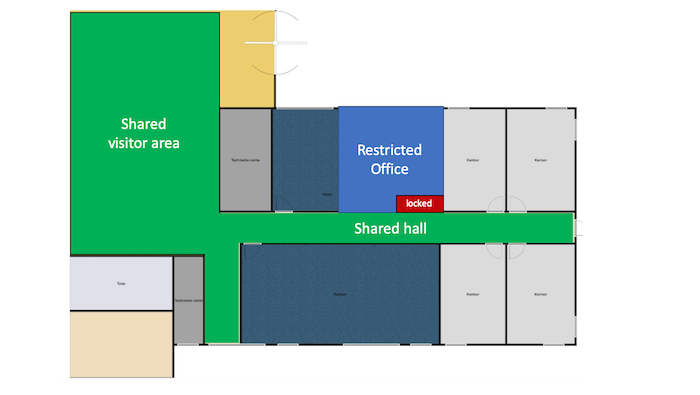
ISO27002:2022 explained – Physical controls
In this article, we explain the new ISO 27002:2022 chapter 7 – Physical controls. This covers the controls necessary to protect information from physical threats. This is the third article in a series of four, each article covering one chapter: organization controls (chapter 5) people controls (chapter 6) physical controls (chapter 7)- This article technological…
Suzanne Atkins
