Blog vulnerabilities

Information Security – Incident management & template incident register
Information Security is a continuous effort; staff handling information needs to be trained regularly, systems need updating to remain secure, assets and risks change, and incidents need addressing. A complete risk register gives you a good idea of what might happen, but without a plan for both anticipated and unanticipated incidents there is a good…
Joost Krapels
The new OWASP top 10 of security vulnerabilities
The Open Web Application Security Project is a very successful free initiative to make Internet Applications more secure. The best known OWASP project is the OWASP top 10, a list of the most common application security vulnerabilities. This top 10 is updated every four years, and the latest 2017 op 10 was published on November 20th.
Sieuwert van Otterloo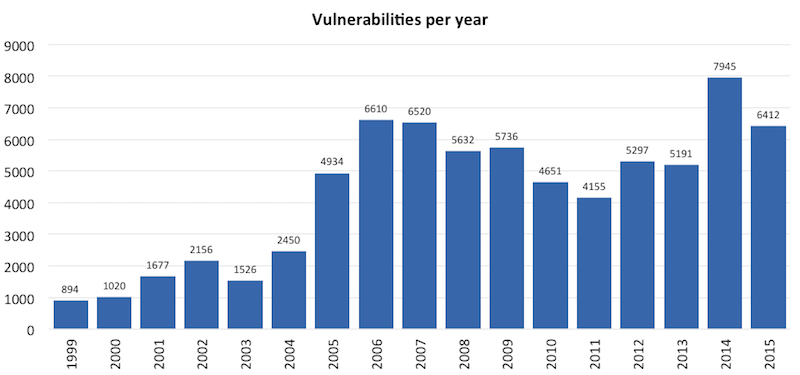
Fewer security vulnerabilities found in 2015
Finally some good news on IT security: The total number of IT security vulnerabilities was 20% lower than in 2014, according to ICT Institute analysis based on CVE data. Apple was the most vulnerable vendor and the iPhone OS and Mac OS X were the most vulnerable products.
Sieuwert van Otterloo
