The new OWASP top 10 of security vulnerabilities
| Sieuwert van Otterloo |
Security

The Open Web Application Security Project is a very successful free initiative to make Internet Applications more secure. The best known OWASP project is the OWASP top 10, a list of the most common application security vulnerabilities. This top 10 is updated every four years, and the latest 2017 op 10 was published on November 20th.
Why the OWASP top 10 is important
The OWASP top 10 is a very important standard for software product quality. Without referring to OWASP, it is hard to specify that software should be secure. In many IT-contracts, the security acceptance criteria are not clear. With OWASP, one can contractually agree that any IT system should be at least OWASP top 10 proof. This means that the system does not contain any of the top 10 vulnerabilities.
Referring to OWASP provides assurance to software users that the software meets basic security expectations. For security-testers it provides a useful structure for security testing and reporting. There are of course more security standards, but somehow they are not as useful as the OWASP top 10: The official ISO 25010 standard for software quality provides quality aspects, but does not specify quality levels. ISO 27001 only applies to organisations and not to products. PCI-DSS is useful but is only applicable to credit card software. For this reason, we believe any developer of online systems and any information security team member should know the OWASP top 10. In our own projects, we also use OWASP to define minimum security expectations. For instance when doing IT Due Diligence , we look for indications that OWASP top 10 vulnerabilities are present. In our Security Verified approach we verify that knowledge about OWASP is present.
The new OWASP top 10 2017
The new OWASP top 10 consist of the following 10 vulnerabilities. These are all vulnerabilities that are often found in online systems. All of these can be easily fixed once they have been identified. The reason many vulnerabilities exist is that developers make mistakes, and systems are not fully tested before they are put into production.
Below are all the top 10 vulnerabilities with their official description:
A1 Injection – Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization
A2 Broken Authentication – Application functions related to authentication and session management are often implemented incorrectly, allowing attackers to compromise passwords, keys, or session tokens, or to exploit other implementation flaws to assume other users’ identities temporarily or permanently.
A3 Sensitive Data Exposure – Many web applications and APIs do not properly protect sensitive data, such as financial, healthcare, and PII. Attackers may steal or modify such weakly protected data to conduct credit card fraud, identity theft, or other crimes. Sensitive data may be compromised without extra protection, such as encryption at rest or in transit, and requires special precautions when exchanged with the browser.
A4 XML External Entities (XXE) – Many older or poorly configured XML processors evaluate external entity references within XML documents. External entities can be used to disclose internal files using the file URI handler, internal file shares, internal port scanning, remote code execution, and denial of service attacks.
A5 Broken Access Control – Restrictions on what authenticated users are allowed to do are often not properly enforced. Attackers can exploit these flaws to access unauthorized functionality and/or data. Think of access other users’ accounts, view sensitive files, modify other users’ data, change access rights, etc. Note that PEN-testers must get test accounts to any systems they would like to test in order to test for this vulnerability. One cannot test without some level of access.
A6 Security Misconfiguration – Security misconfiguration is the most commonly seen issue. This is commonly a result of insecure default configurations, incomplete or ad hoc configurations, open cloud storage, misconfigured HTTP headers, and verbose error messages containing sensitive information. Not only must all operating systems, frameworks, libraries, and applications be securely configured, but they must be patched and upgraded in a timely fashion.
A7 Cross-Site Scripting (XSS) – XSS flaws occur whenever an application includes untrusted data in a new web page without proper validation or escaping, or updates an existing web page with user-supplied data using a browser API that can create HTML or JavaScript. XSS allows attackers to execute scripts in the victim’s browser which can hijack user sessions, deface web sites, or redirect the user to malicious sites.
A8 Insecure Deserialization – Insecure deserialization often leads to remote code execution. Even if deserialization flaws do not result in remote code execution, they can be used to perform attacks, including replay attacks, injection attacks, and privilege escalation attacks.
A9 Using Components with Known Vulnerabilities – Components, such as libraries, frameworks, and other software modules, run with the same privileges as the application. If a vulnerable component is exploited, such an attack can facilitate serious data loss or server takeover. Applications and APIs using components with known vulnerabilities may undermine application defenses and enable various attacks and impacts.
A10 Insufficient Logging & Monitoring – Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems, and tamper, extract, or destroy data. Most breach studies show time to detect a breach is over 200 days, typically detected by external parties rather than internal processes or monitoring.
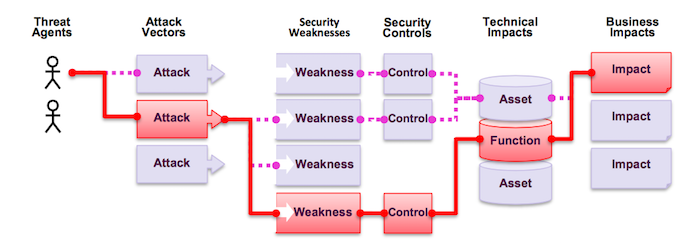
OWASP definition of vulnerability
OWASP uses an attack model to estimate the risks of certain vulnerabilities. The model is shown below. It assumes that certain threat agents (different types of hackers) use attack vectors to search for vulnerabilities. If they found one, the damage they can do will depend on the controls. If there are insufficient controls (e.g. logging or detection) there will be technical impact (a server taken over) and ultimately business impact (economic damage or money stolen).
The changes explained
The top 10 is updated every four years, based on community feedback. The new 2017 top 10 is quite similar to the top 10 of 2013. The image below shows that the top 10s are mostly similar. Six (in white) are the same.
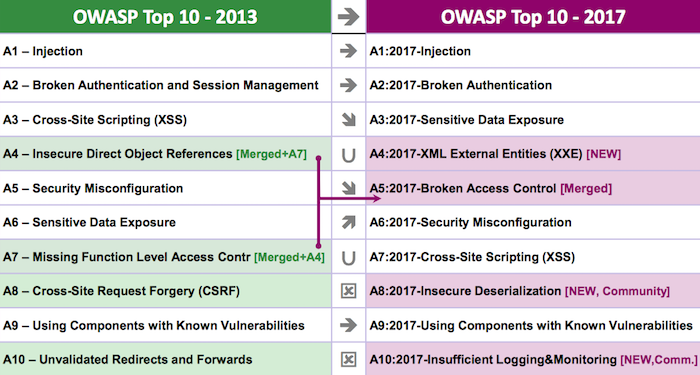
Two issues have been merged and two issues are no longer top 10 issues. In the case of CSRF (cross site request forgery) there is real progress. The use of newer, better frameworks that offer structural solutions have made CSRF a much smaller problem. The other vulnerabilities (unvalidated redirects and forwards) are still dangerous but have been pushed out of the top 10 by newer, more worrisome issues.
One of the new items is an odd one that is hard to test: “insufficient logging and monitoring” is not a vulnerability that can be detected from the outside. This is also not something application developers are responsible for. Instead the system owner should organize monitoring. Some narrow-focus PEN-testers and security tools will skip this in their testing. Security teams however should pay attention that adequate monitoring is in place.
How to use this new top 10
Any security team should communicate this new top 10 to their software development teams and ask them to study the new top 10 closely. The PDF document from this page gives complete descriptions of each vulnerability and is the source of the descriptions and images. In the same document there are also many pointers to additional information. A good overview of other worthwhile OWASP projects is this list of OWASP flagship projects.
When organizing a PEN-test or using OWASP in a contract, make sure that you specify which OWASP top 10 version is used. We recommend to use the OWASP top 10 2017 from now on until 2021.
Dr. Sieuwert van Otterloo is a court-certified IT expert with interests in agile, security, software research and IT-contracts.

