Time stamping files using bitcoin and blockchain
| Sieuwert van Otterloo |
Security

Bitcoin or blockchain technology can be used for creating secure time-stamped digital signatures. We show an easier way to do this that works today, without the need for any third party website.
Bitcoin is more than a virtual currency. The technology (blockchain), can be used for securing all types of real world transactions. One of the most promising applications is time-stamping documents, proving that documents were created on a certain date and not changed afterwards. A first service for this was launched in 2013 (www.proofofexistence.com) and covered in Forbes and business insider as an example how bitcoin is changing the world.
Such a timestamping service has many security applications that are of interest to ICT Institute. Classical use of such a service would be a digital notary, verifying contracts. New uses include secure distribution of software, proving copyright on written stories and also securing files against changes. In the forensic world it is important to have solid digital evidence. Timestamped audit files would provide definite proof that an intrusion has taken place at a certain time.
We looked at using an existing service such as www.proofofexistence.com for securing log files, to build one of the first security applications of bitcoin. We discovered however that this service is not easy enough to use in practice. One needs to rely on a special website to look up information in the blockchain. This makes the method less transparent and ultimately less convincing. We therefore decided to create a simpler way of signing documents that runs without any specialized website. The method of timestamping we propose can be executed with any bitcoin wallet, from any computer, without any website in between. It is a truly open method. In the examples we use the web API from blockchain.info, but one could use any other bit current exchange service for our example.
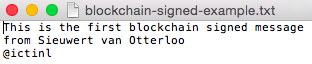 We use the following file blockchain-signed-example.txt as an example document that we want to timestamp. Below we explain how you could sign this document and how you validate our signature on the document.
We use the following file blockchain-signed-example.txt as an example document that we want to timestamp. Below we explain how you could sign this document and how you validate our signature on the document.
Timestamping a document
All digital signatures make use of hash functions (also called one way functions). These functions take any file and compute a fixed length fingerprint: a code that identifies the file. Anyone with the file can generate the code, it is practically impossible to construct the file from the code. Bitcoin internally uses the hash codes for addresses. To timestamp a file, you need to compute the code and use the code in a bitcoin transaction. Because bitcoin has an open transaction ledger, anyone can then see the code. Our method uses the standard, proven hash function SHA-1 that is also used in bitcoin.
 One can use the mac command “shasum blockchain-signed-example.txt” to compute the hash: it is 3a472c5409d82aa361275e276cdc1116cdba594e . Ideally we would use this hash code in a comments field in a bitcoin transaction. However, bitcoin does not have a clear comments field that is visible to anyone. Basic bitcoin transactions just have a from-field, a to-field and an amount. We are therefore going to use the hash as the two-field. We are going to send a small amount to the code of our document. We compute the address as a standard hash function: https://blockchain.info/q/hashtoaddress/3a472c5409d82aa361275e276cdc1116cdba594e
One can use the mac command “shasum blockchain-signed-example.txt” to compute the hash: it is 3a472c5409d82aa361275e276cdc1116cdba594e . Ideally we would use this hash code in a comments field in a bitcoin transaction. However, bitcoin does not have a clear comments field that is visible to anyone. Basic bitcoin transactions just have a from-field, a to-field and an amount. We are therefore going to use the hash as the two-field. We are going to send a small amount to the code of our document. We compute the address as a standard hash function: https://blockchain.info/q/hashtoaddress/3a472c5409d82aa361275e276cdc1116cdba594e
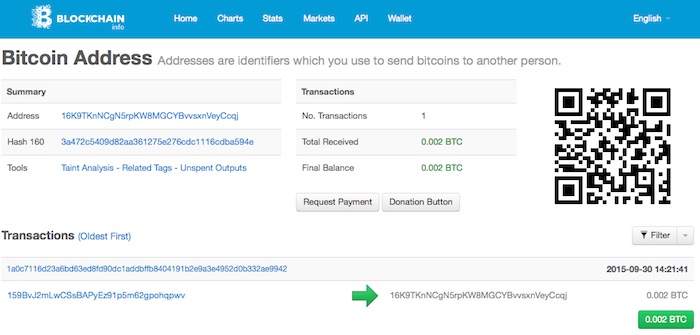
This returns the bitcoin address: 16K9TKnNCgN5rpKW8MGCYBvvsxnVeyCcqj We have sent a small amount to this address. We recommend any value between 0.0001 (2 dollarcent) and 0.002 bitcoin (50 dollarcents, used in this example). [If you have suggestions for practical guidelines, please let us know. ]
Checking a signature
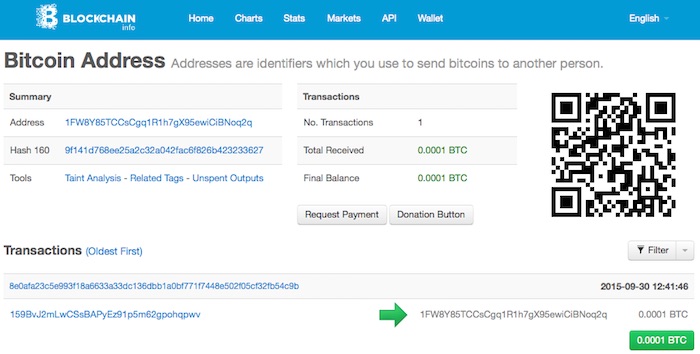
Suppose that you have received or downloaded the document and want to verify its authenticity. Specifically you want to know for certain that your version is exactly the sme as the original from 30 sept 2015. You use the mac command “shasum blockchain-signed-example.txt” to compute the hash: it is still 9f141d768ee25a2c32a042fac6f826b423233627. You again compute the bitcoin address of the hash: https://blockchain.info/q/hashtoaddress/3a472c5409d82aa361275e276cdc1116cdba594e. This again returns 16K9TKnNCgN5rpKW8MGCYBvvsxnVeyCcqj
Now you check the status of this address by going to the following page: https://blockchain.info/address/16K9TKnNCgN5rpKW8MGCYBvvsxnVeyCcqj
As you can see our document was signed on 2015-09-30, as this is the date of the first and only bitcoin transaction to this address. This proves that someone has computed the 16K..qj address, and this proves that someone had our file with the hash code 3a…94e (see the Hash 160 at the top right of the screen).
Usefulness and limitations
The protocol we presented is as secure as the building blocks used. Bitcoin and the SHA1 hash function. Both are welltested in practice. The SHA1 function itself is a reliable but older hash function with medium security, as it only has 160 bits. It is much safer than MD5, another commonly used hash function. In theory one can generate multiple versions of documents that have the same 160 bit hash. This would however be very expensive in terms of computing power. If you use this protocol not for a once-a-year document but for daily logs, it is unlikely that people spend the considerable computer resources to falsify SHA1 hashes every day.
An interesting property of the protocol is that it ‘burns’ bitcoins. By sending bitcoins to a non-existent address, these bitcoins become unspendable. If one needed to sign a large number of files and does not want to use so much bitcoins, one can combine the hashes of all documents to be signed in a single document and only sign that document.
We would like to point out that time stamping guarantees existence of a document but does not prove ownership. To prove this point we took a haiku from an existing bitcoin discussion and signed it using the method from this article: since we had this document signed it seems like we wrote and claim ownership of this haiku. This is however not secured: we only prove that this haiku is older than a certain date, not who wrote it or owns it.
Next steps
We published this protocol description to create a simple and open timestamping service for anyone. Use of this protocol is free of charge, but please refer to our website as the origin of the protocol.
We would love to hear comments and questions about the protocol. If you are going to use it in a service, let us know and we will add you to the list of services using this method of timestamping. Also if you have alternative services / uses or a similar services, let us know so we can list this as an alternative.
Within ICT Institute we are helping customers to make their IT systems more secure. If you would like our help, either for securing log files or for overall security advice, feel free to contact us.
Dr. Sieuwert van Otterloo is a court-certified IT expert with interests in agile, security, software research and IT-contracts.