How to improve your internet.nl score
| Joost Krapels |
Security

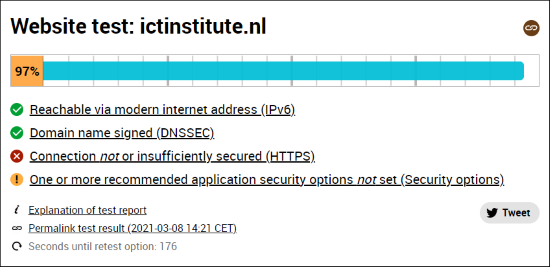
Internet.nl is a service, co-created by the Dutch Government, for measuring the security of your website. The tool summarises many security aspects into two simple scores: one for websites and one for email. We use the service quite a lot, both for ICT Institute and our clients. Each score is between 0% and 100%. If your organisation scores higher than 70%, you are doing quite well. If not, make sure to follow the steps in this article so your clients can securely interact with you.
Internet.nl Website test
To calculate what your score out of 100 is, Internet.nl takes the following into account:
- IPv6, which is the updated IP address protocol
- DNSSEC, which protects your visitors from being (mis)directed to malicious websites
- HTTPS and TLS, encrypting traffic to make it unreadable for eavesdroppers
- Security headers, telling browsers what may and may not be done with your website
IPv6
The most well known type of IP-addresses are IPv4 addresses, which look like this: 192.168.0.1. When these were first introduced, the 4.3 billion unique options this provides seemed plenty. Around 2011 we started running out of IPv4 addresses and IPv6 was formally introduced. These addresses look like 2a01:7c8:eb:0:149:210:209:157 , and allow for 430 undecillion (that’s 430 with 36 zeroes) unique options. If your website can be reached through IPv6, it’s future ready.
To have your website work with IPv6:
- Choose a registrar that supports IPv6. The SIDN has a search tool on their website, which allows you to select recognized registrars and filter them. At ICT Institute, we use TransIP. Other registrars with both IPv6 and DNSSec are hostnet.nl, hosting.eu and easyhosting.nl.
- Next, choose a hosting provider that supports IPv6 as well. Many registrars, such as the ones mentioned above, offer hosting services as well.
- Finally, configure your website for IPv6 in the DNS-settings of your registrar. They often have dedicated articles on how to do this.
DNSSEC
DNSSEC is a technology that protects the process of providing your browser with the website you requested. With this technology active, it becomes much more difficult for malicious actors to provide the browser of your visitors with a different website than yours.
Having DNSSEC requires your registrar to support the technology. The SIDN tool we mentioned earlier also has a filter for DNSSEC, so we recommend switching on both filters before choosing a registrar. Supporting registrars should have DNSSEC enabled by default, but if not, their website or helpdesk will sort you out.
HTTPS and TLS
You should make sure your server uses the secure version https, and not the old version http. For this, you need to have TLS (Transport Layer Security) certificate. A TLS certificate is available for free at Let’s Encrypt, or can be purchased in paid form from your registrar or via the software you used to build your website (such as WordPress). Installing the TLS certificate takes place at your hosting provider.
Note: TLS certifcates expire after a certain period. Make sure you have switched on automatic renewal!
Security headers
When a visitor requests your website, the visitor’s browser receives the content of the website plus some extra information for the browser. This extra information is called the HTTP header, and they can contain some security rules the browser has to follow. Security headers need to be manually configured at your hosting provider. KeyCDN wrote a great article on security headers, explaining in more detail what they are and how to configure them.
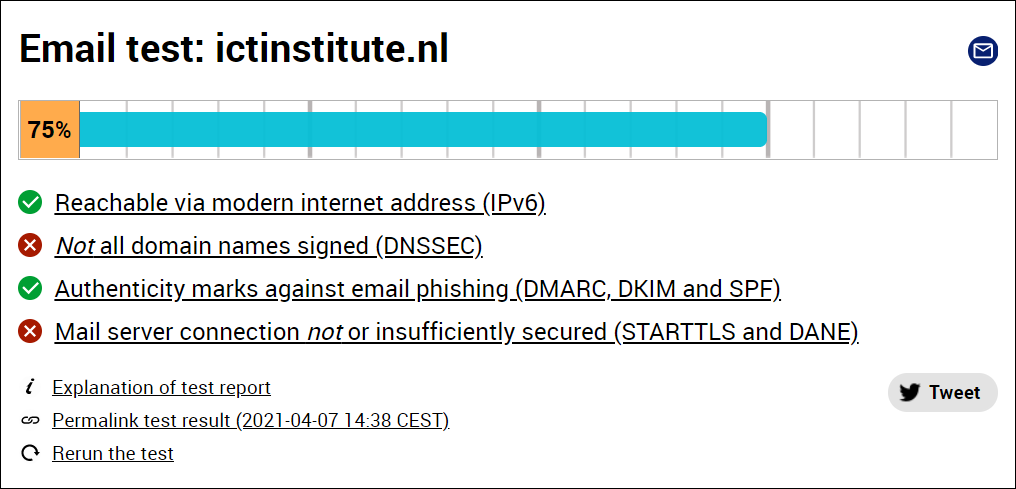
Internet.nl Email test score
To calculate what your score out of 100 is, Internet.nl takes the following into account:
- IPv6, which is the updated IP address protocol
- DNSSEC, which protects emails from being routed to malicious actors
- SPF, DKIM and DMARC to protect against spoofing
- STARTTLS and DANE, for encrypting email traffic
IPv6
If you’ve read the first half of the article, you will be familiar with IPv6. The internet architecture for emails is, however, slightly different than the one for websites. Where websites need to be stored on and communicate from a web server, emails are stored on and communicated from a mail server. Web servers and mail servers are, however, similar in the fact that they benefit from having an IPv6 address.
If you chose a registrar that offers IPv6, you are already halfway there. The new part is choosing a mail provider that offers mail servers with IPv6 capabilities. Two commonly used mail providers for larger organisations, Microsoft (365) Exchange and Google Suite, do. During the coupling of your mail provider with your domain, which is done in the DNS settings at your registrar, you simply need to enter the names of the mail servers as described by your mail provider. We recently wrote a (Dutch) article on basic domain security, which you might find interesting.
DNSSEC
Just like IPv6, DNSSEC is a security measure for both website and email traffic. Also, just like IPv6, the only difference between using it for website traffic and email traffic is the fact that emails use mail servers instead of web servers. In this case, DNSSEC protects the integrity of the destination.
To make DNSSEC fully functional, both the registrar and mail provider need to support DNSSEC. For those using Google Suite, using the mxX.smtp.goog mail servers instead of the standard altX.aspmx.l.google.com., as described in this article on bornoe.org, should do the trick. Be aware that making an error while switching mail servers when your organisation is operational might impact the availability of emails for more than a day.
SPF, DKIM and DMARC
Email has several inherent flaws (or features if you prefer that) in its design that make it possible to trick receivers into thinking the email is sent by a certain person or organisation. This technique can be used for benign goals, but you should protect your clients against those with more malignant intentions.
With SPF, you inform all mail servers receiving emails “from” your domain which organisations may pretend to be you and which may not. You might, for example, want to allow SendGrid to use your email address as the sender of mass mails.
DKIM allows you to add an invisible unique digital signature to all emails that are sent from your domain. To add a DKIM record, you request the record from your mail provider and publish it in your DNS records. Google wrote a great manual explaning how to do this for Google Suite.
DMARC combines the input of both SPF and DMARC, and tells mail servers receiving emails “from” your domain what to do with emails that don’t pass the tests. Mails can be automatically marked as spam, or even rejected. DMARC can also create useful reports for you, allowing you to fine tune your SPF record. We recommend using DMARCIAN’s DMARC record creation tool to create a valid record.
Checking whether your SPF, DKIM and DMARC records work correctly can be done through internet.nl, but free tools on DMARCIAN’s website provide more information and help to get it right.
STARTTLS and DANE
STARTTLS solves the same problem for email traffic as HTTPS solves for website traffic: adding TLS encryption because there is none by default. DANE is a security measure that works together with DNSSEC, verifying the origin of TLS certificates.
For STARTTLS and DANE, you need DNSSEC for your mail servers. Once you have DNSSEC correctly configured, check whether you mail provider offers STATTLS and configure it accordingly.
Deploying DANE is slightly more challenging than the other security measures above. It requires you to publish a so-called TLSA record. We currently have no experience doing this, but will update the article when we do!
Image source: @henry_be via Unsplash
Info source: internet.nl, internetsociety.org, dmarcian.com, keycdn.com, bornoe.org
Joost Krapels has completed his BSc. Artificial Intelligence and MSc. Information Sciences at the VU Amsterdam. Within ICT Institute, Joost provides IT advice to clients, advises clients on Security and Privacy, and further develops our internal tools and templates.