ISO 31000 in relation to ISO 27001
| Jelle Hoekstra |
Security

Risk management plays a very important role in an ISO 27001 Information Security Management System (ISMS). At the end of paragraph 6.1 “Actions to address risks and opportunities” there is however a reference to a fairly unknown norm ISO 31000. What is the relationship between ISO 31000 and ISO 27001? In this blog we briefly explain the relationship between these two norms and provide you with some insights concerning risk management gained from reading ISO 31000.
The short answer is: the risk assessment and treatment process in ISO 27001 aligns with the principles and generic guidelines provided in ISO 31000. What does this alignment entail?
ICT Institute already published an article on A basic risk management method for information security. In that article we’ve described a basic method to manage risks. It is important to realize that risk management is an activity and term that is not reserved for information security only. Risk management also plays an important role for example in finance, project management and health care. In ISO 31000 principles and generic guidelines have been set out for risk management in all those different area’s.
The risk management process of ISO 27001 consists of two important aspects:
- Information security risk assessment (par. 6.1.2 ISO 27001)
- Information security risk treatment (par. 6.1.3 ISO 27001)
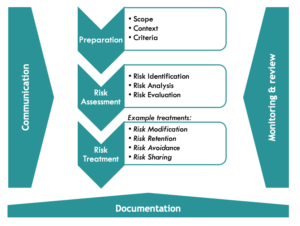
If we look at ISO 31000, we see that after defining scope, context and criteria the process continues with:
- Risk assessment (par. 6.4 ISO 31000)
- risk identification
- risk analysis
- risk evaluation
- Risk treatment (par. 6.5 ISO 31000)
- selection of risk treatment options
- preparing and implementing risk treatment plans
Tips on drafting a risk management process
As we’ve already explained in A summary of ISO 27001 requirements for information security: regrettably the ISO standard are not freely available, making it harder than necessary to look up what is actually required. While we still recommend you to read the full standard, we provide you with some insights gained from reading ISO 31000:
- Information security risk management should not be isolated from other risk management in the organization (for example, with regard to finance).
- Risk is defined as “effect of uncertainty on objectives”. This can either be positive or negative and therefore can apply to opportunities and threads. This is often neglected and we only focus on threats.
- A risk management process has an initial phase (the first time you perform it) and should afterwards be regularly maintained (review & monitoring). This is explained in paragraph 6.6 of ISO 31000 and you can also see it in the index of ISO 27001:
- Chapter 6 “Planning” (initial phase) consists of:
- Information security risk assessment (par. 6.1.2 ISO 27001)
- Information security risk treatment (par. 6.1.3 ISO 27001)
- Chapter 8 “Operation” (maintenance) consists of:
- Information security risk assessment (par. 8.2 ISO 27001)
- Information security risk treatment (par. 8.2 ISO 27001)
- Chapter 6 “Planning” (initial phase) consists of:
- You can also follow the methodology in the third norm ISO 27005. Note however that these are guidelines and not mandatory norms on how to draft your risk management process. If you want a lean and mean risk management process: just follow the steps in par. 6.1.2 & 6.1.3 of ISO 27001.
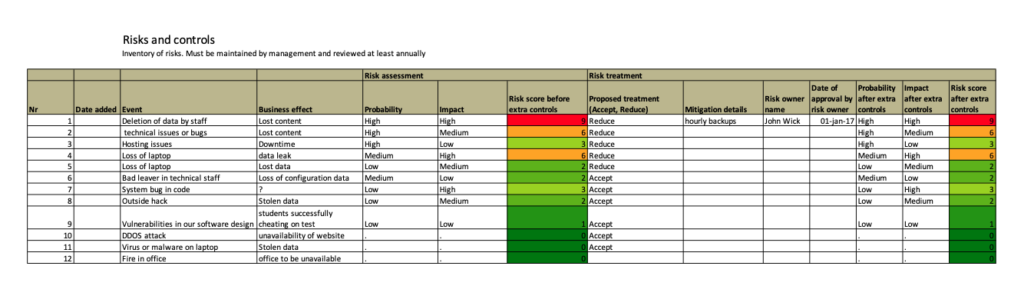
- It is a good practice to use the ‘official’ terms from the norm in your risk register. This way it is more easy to explain your risk methodology, for example to a certification auditor. This could look something like this:
Example risk register
For more articles about information security, visit this page. Contact us if you want more information or advice on setting up your risk management process.
photo credit Hush Naidoo on Unsplash
Jelle Hoekstra LLM is consultant and mediator at ICT Institute. He is a certified privacy professional (CIPP/E & CIPM), security consultant (ISO27001 Lead Auditor) and IMI Qualified Mediator. Before he worked at several organisations as legal advisor and Privacy & Security Officer. Jelle is member of the International Association for Privacy Professionals (IAPP), the Dutch association for Data Protection Officers (NGFG, Nederlands Genootschap voor Functionarissen van Gegevensbescherming) and member at the International Mediation Institute (IMI).