Information security – asset inventory
| Sieuwert van Otterloo |
Security

One of the first steps in setting up an information security management system is to create an inventory of information assets. It is in important step to make sure the right measures will be taken: the assets are the basis for identifying risks, and thus for the measures that will be taken to mitigate risks.
What is an information asset?
As information asset is any valuable information that the organisation has. Valuable here means that the organisation either acquired it at some cost, is actively using it now in some process or could use it for some purpose in the future. The definition of an asset is deliberately wide: it is important to recognize all kinds and types of assets.
An information assets can have many different forms: it can be a paper document, a digital document, a database, a password or encryption key or any other digital file.
Each asset is stored on some carrier like paper, a USB stick, hard drive, laptop, server, cloud or backup tape. It is not necessary to also identify all carriers. However if you believe that you might have specific risks that depend on the type of carrier (e.g. for data on USB stick or paper documents) you can add ‘other information on USB sticks’ as an asset to make sure your inventory is complete. The risk inventory is a tool that should help you understand and improve security.
What is in the inventory?
In order to comply with information security best practices, there is some minimal required information per asset. We have listed these items below. It is allowed to add additional fields to make the inventory more useful to your organisation.
The required fields are:
- Name and description: it should be clear for people inside the company what is meant
- Owner: Each asset must have an owner that will take final decisions on what should happen with the asset. It should be a business owner: the IT departement or information security team should not be owner of any asset. Typically the owner is a director or senior manager, since the owner must also provide the budget for managing or improving the asset.
- CIA. Information security is defined as confidentiality, integrity and availability of information. You should make clear which of these three apply to your asset. For many assets it is all three (label: CIA). For published information confidentiality is not an issue so they should be labeled IA.
- Personal data: There are in most countries special rules for the treatment of personal data. This data should have additional protection. It is important to understand which assets contain personal data so that anyone can check whether these assets have this additional protection.
- Access. It is not acceptable to give anyone in an organisation access to all assets. For instance PCI-DSS explicitly forbids such a simple access model. You need to define roles (e.g. customer service, developers, operations staff, directors, HR) and specify using these roles who should have access.
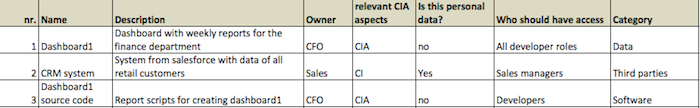
The illustration below shows what a minimal inventory could look like. It is a screenshot of our assets-risks excel template. Excel or another spreadsheet program, in combination with a shared drive, dropbox or cloud account is one way one can maintain the assets risks inventory.
Asset categories
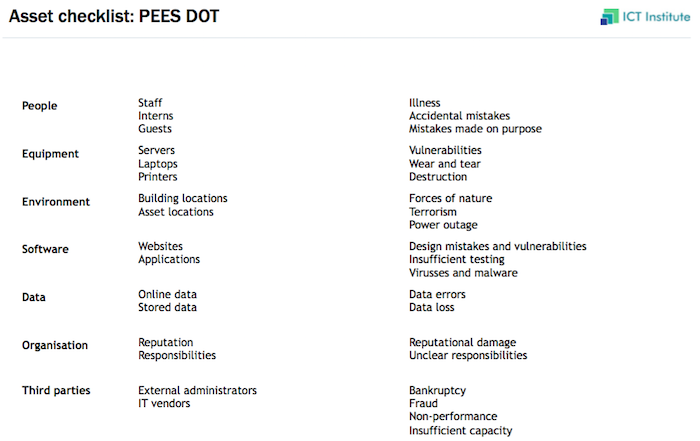
In order to discover all information assets, it is useful to use categories for different types of assets. The categories can be used as a checklist, to make sure one has thought of all aspects. We use ‘PEES DOT’ as a simple categorisation, both for risks and assets (see our risk assessment approach). The category descriptions are:
- People: Information accessible to one person or linked to unique role
- Equipment: Information inside or generated on/by specific devices
- Environment: Information linked to factors outside the company, e.g. city, region
- Software: Information stored by single IT systems
- Data: Structured information not linked to one software system. Includes user generated content
- Organisation: Any information about the organisation, e.g. org structure, processes
- Third parties: Information from or managed by specific suppliers, customers or partners
If you involve people from all departments, and you ask them to think about all the PEES DOT aspects, you should get a complete overview of all assets. There are probably some assets that fit into multiple categories (e.g. database for specific software). This is not a problem, just pick a category that fits well. PEES DOT is not mandatory but a useful tool for discovery.
How to make the asset inventory
Creating the asset inventory is one of the first actions of an information security team. When we help teams with information security, we often make a first start in a workshop with the information security team and some representatives from management. This makes sure that team and management get a common understanding of information security priorities. The process can be an informal scrum process: participants first write down their input for themselves. Then they share their results. After the workshop, the information security team completes and maintains the information assets inventory.
The inventory should be updated when additional assets are uncovered. New assets are often discovered in risks workshops (see this article on risk management), because each risk is typically linked to an asset. Each time this happens, the information asset inventory should be extended with the new asset.
The information asset inventory should be validated regularly by the management and the asset owners. Management should check that all assets that they know of and care about are present. The asset owners should check whether they recognize and understand all assets that are assigned to them, and are willing to be responsible for investment decisions for these assets.
Maintaining the asset inventory
The asset inventory should be updated continuously by the information security team based on new assets, risks, workshops, incidents and questions from other staff. It must be validated regularly by management and owners, for instance every quarter or every six months. We recommend to plan a regular information security review meeting, where one of the items on the agenda is the information asset inventory.
Further reading
This article is part of a series of blog post on information security and information security certification. The recommended reading order is:
- Security basics: Asset inventory, Risk assessment
- Example measures: password policy, two factor authentication
- Legal requirements: reporting data breaches
- Certification: criteria, review process
- Other resources
For more articles about information security, visit this page.
Image source: Wikimedia commons – JoJan
Dr. Sieuwert van Otterloo is a court-certified IT expert with interests in agile, security, software research and IT-contracts.